- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- UI Extensions
- Service Checks
- IDE Integrations
- Community
- Guides
- API
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Synthetic Monitoring
- Continuous Testing
- Mobile Application Testing
- Software Delivery
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- Log Management
- Observability Pipelines
- Log Management
- Administration
Connect your AWS Account to Cloudcraft
Connecting your AWS accounts to Cloudcraft allows you to visualize your infrastructure by reverse-engineering the live environment’s service relationships into a system architecture diagram. In addition to automatically generating diagrams, a budget model will also be created, and your imported components will display live status data directly in your diagrams. There is no limit on the number of AWS accounts you can connect to Cloudcraft.
Note: For AWS organizations, you must manually add the Cloudcraft role to each individual account in the organization.
This article walks you through connecting your AWS account to Cloudcraft.
Requirements
- A Cloudcraft user with the Owner or Administrator role.
- An active Cloudcraft Pro subscription.
- An AWS account with permission to create IAM roles.
How the live AWS sync works
Cloudcraft uses a cross-account role to securely access your AWS environment. As a result, you need to create a Cloudcraft-specific, read-only role in your AWS account. This role can be revoked at any time.
If having a read-only role with access to all components isn’t permissible or violates your company’s policies, you also have the option to attach a stricter minimal access policy, only giving read-only access to the resources you want to use with Cloudcraft, further minimizing the amount of data the role can access.
Cloudcraft doesn’t keep any of the live data from your AWS environment. Instead, it stores ARNs, which are unique identifiers for resources in AWS. This allows the application to link live data to components at runtime.
The data from your AWS environment is streamed in real-time to your browser via Cloudcraft’s own AWS environment via role-based access, and is only stored client-side while you are using the application. When you close the application, the live data is deleted.
While not having write access to your account prevents Cloudcraft from offering certain features—like deleting an EC2 instance on both the diagram and your account—it’s simply a more secure approach.
Cloudcraft implements rigorous security processes and controls for the SOC2 compliance program. You can read more about Cloudcraft’s security program and controls on the security page.
Manage AWS accounts
Add account
- In Cloudcraft, navigate to User > AWS accounts.
- At the bottom of the modal, click Add AWS Account.
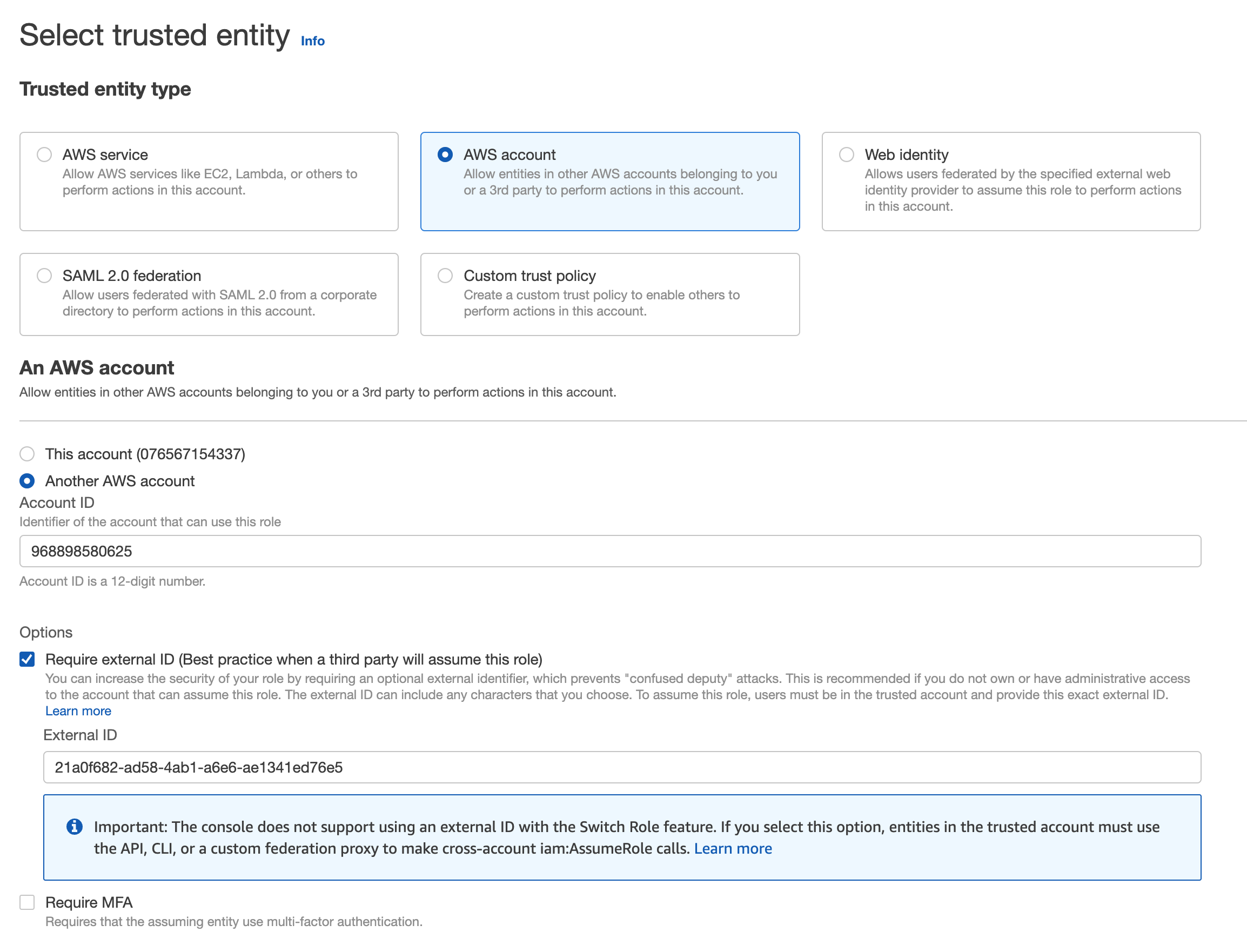
- The next page provides step-by-step instructions. Click Open the AWS IAM Console to the Create Role page to configures the read-only IAM role in AWS.
If you can't access the Create Role page, you may lack AdministrativeAccess or sufficient IAM permissions to create a new IAM role. If this is the case, contact your AWS account's administrator and have them complete the following steps.
- On the Create role page in AWS, leave Require MFA unchecked, and click Next.
Require MFA must be disabled as it's not applicable for system-to-system access where there is no human involved. Access is instead protected by being limited to access from the Cloucraft AWS account.
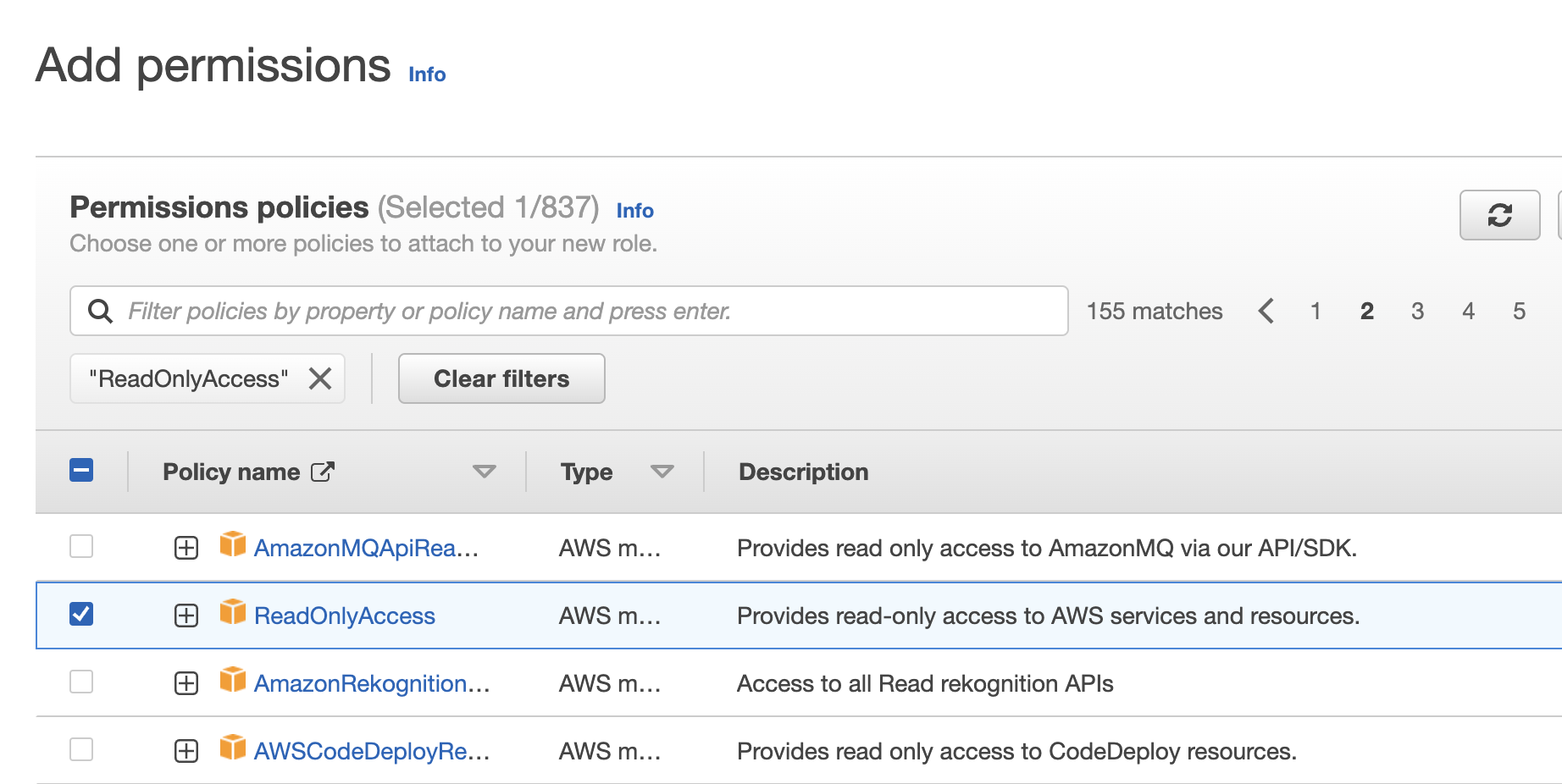
- Next, add permissions policies to your role. Type ReadOnlyAccess in the search box and press Enter to filter policies by name.
- Select the ReadOnlyAccess policy that provides read-only access to AWS services and resources, then click Next.
- Enter a name and description for the IAM role. You can also add tags to organize, track, or control access for the role. Tagging your role is optional. For tagging best practices, see Best Practices for Tagging AWS Resources.
- Click Create role.
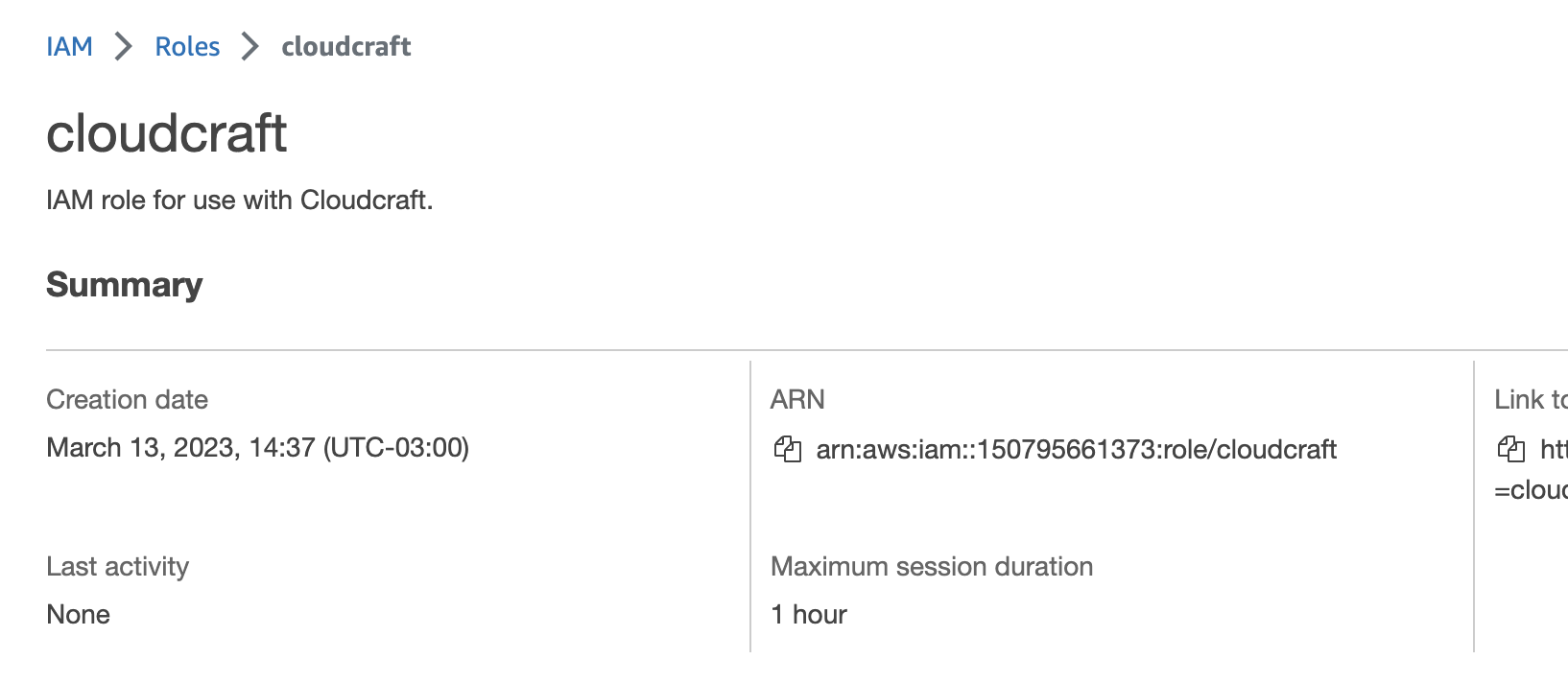
- Select the
cloudcraftrole from the list of roles. On the Summary page, copy the Role ARN.
- In Cloudcraft, paste the ARN in the Role ARN field, and enter a name for your account.
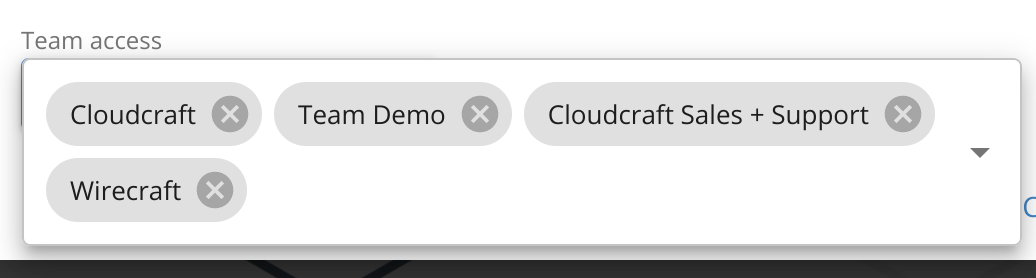
- Optionally, configure team access by clicking the blue button beneath Team access and selecting the teams you want to share access to the AWS account with.
- Click Save Account.
Edit account
To edit an account, click the gray pencil icon to the left of the account you want to edit. You can change details of the account, such as the name, ARN, and team access.
When you are done, click Save Account.
Remove account
To remove an account, click the trash can icon to the right of the account you want to remove, then click Remove.