- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- UI Extensions
- Service Checks
- IDE Integrations
- Community
- Guides
- API
- CoScreen
- Cloudcraft
- In The App
- Watchdog
- Bits AI
- Dashboards
- Infrastructure
- Metrics
- Notebooks
- Alerting
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Universal Service Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Software Delivery
- Log Management
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- Digital Experience
- Real User Monitoring
- Synthetic Monitoring
- Continuous Testing
- Mobile Application Testing
- Administration
Create a custom IAM policy to use with Cloudcraft
Cloudcraft uses a read-only IAM role to scan your AWS account and reverse-engineer the service relationships between components to autogenerate a diagram of your architecture.
The easiest way to set everything up is to follow the instructions inside the application, which creates the role and sets up the permissions for you in just a few clicks. The role is assigned the AWS-managed ReadOnlyAccess IAM policy by default.
If you need to more precisely control the permissions, for example to exclude certain services or APIs, a custom Cloudcraft IAM policy will allow you to do that.
If you use a custom IAM policy, you must keep it manually updated as new services and features are added to Cloudcraft. If you see a notice in the app of Limited AWS access, try updating your custom IAM policy with the latest version from below.
Creating a custom IAM policy
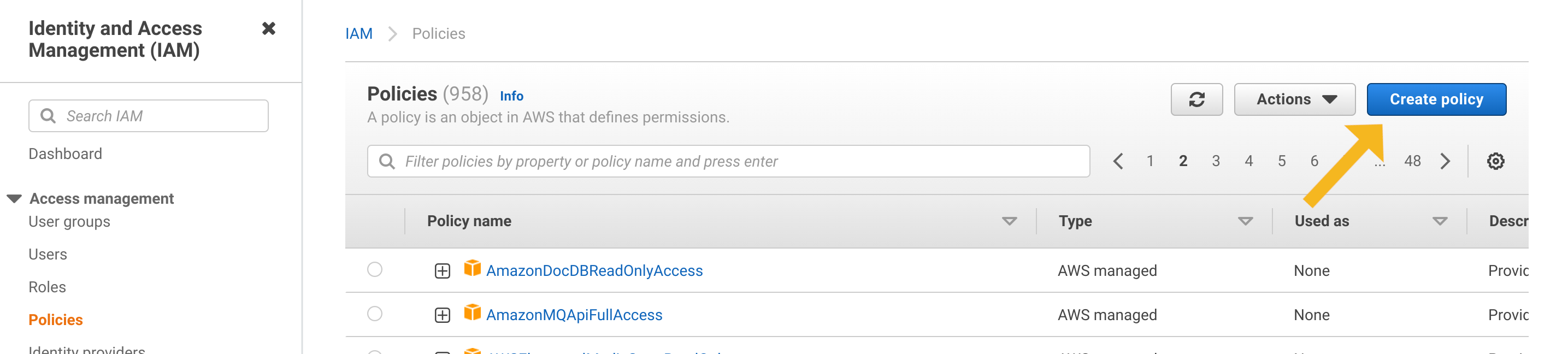
Start by opening the IAM Policies Console and clicking the Create Policy button.
Switch to the JSON tab and copy the content from one the linked policies below:
You can also customize the policy to suit your unique requirements.
- Cloudcraft custom IAM policy: This policy is more strict than the default
ReadOnlyAccesspolicy. The policy only includes the individual services and read-only permissions that Cloudcraft uses. The policy will typically need to be updated when Cloudcraft adds support for entirely new services. - Cloudcraft minimal IAM policy: This is the strictest form of policy. The policy lists each individual read-only permission for full Cloudcraft functionality. This policy needs to be updated more frequently, both when support for new services are added and when existing services are improved.
- You may use either of the policies above as a base for your own customizations. For example, individual services or permissions can be removed. If a service cannot be accessed by Cloudcraft, the service will be excluded from the resulting diagram.
Click the Review policy button at the bottom of the screen, and then enter a name and description. Cloudcraft recommends using the following values to keep things organized and easier to audit.
- Policy Name: Cloudcraft
- Policy Description: Custom policy for Cloudcraft.
Next, click Create policy to create the policy. The AWS console redirects you back to the policies page.
Finally, attach the newly created policy to the Cloudcraft IAM role. If you didn’t create the role yet, follow the instructions in the application.